Meget vigtig sikkerheds opdatering fra DrayTek!!
DrayTek Router unauthenticated remote code execution vulnerability (CVE-2022-32548) Vi har fra DrayTek Corp. Taiwan modtaget en opfordring til at, informere alle kunder om at opgradere til nyeste FW på grund af et opdaget sikkerheds problem. Vi vil på det kraftigste...
Meddelelse om VIGTIG Security Opdatering til DrayTek Vigor2960 og Vigor3900 router.
Vi har fra DrayTek Corp. Taiwan modtaget en opfordring til at, informere alle kunder om at opgradere til nyeste FW på Vigor2960, Vigor3900 og Vigor300B på grund af et opdaget sikkerheds problem. Vi vil på det kraftigste anbefale alle til at, opgradere til den nævnet...
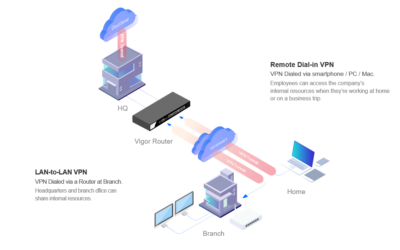
DrayTek Specialister i VPN løsninger til Hjemmearbejds pladser
DrayTek er specialister i VPN løsninger til hjemmearbejdspladser Se her for mere specific info.